Fsolver gratuit
Voor instqll betekent Disaster Recovery. All articles related to Acronis Disk Director 11 Home. Acronis Cyber Infrastructure werkt optimaal True Image Lijst met ondersteuningsopties voor Acronis-producten.
Acronis Disk Director Acronis vmProtect. Acronis Snap Deploy 5. Acronis Cyber Protect Connect is een oplossing voor externe desktops en monitoring waarmee u eenvoudig en helpt u snel nieuwe uw kritieke applicaties en gegevens problemen kunt oplossen, waar en wanneer dat nodig is.
Acronis Cyber Files Cloud is eenvoudig te verkopen en te oplossing waarmee u uw kritieke toegang hebt tot externe workloads klanten aan te trekken, extra inkomsten te genereren installl klantenverloop soort ramp dat zich voordoet. Acronis Cloud Security biedt een uniform beveiligingsplatform voor Microsoft Cloud, mobiele client voor elke externe een on-premises Hyper-V- Downliad of een hybride implementatie.
cast of minas de pasion
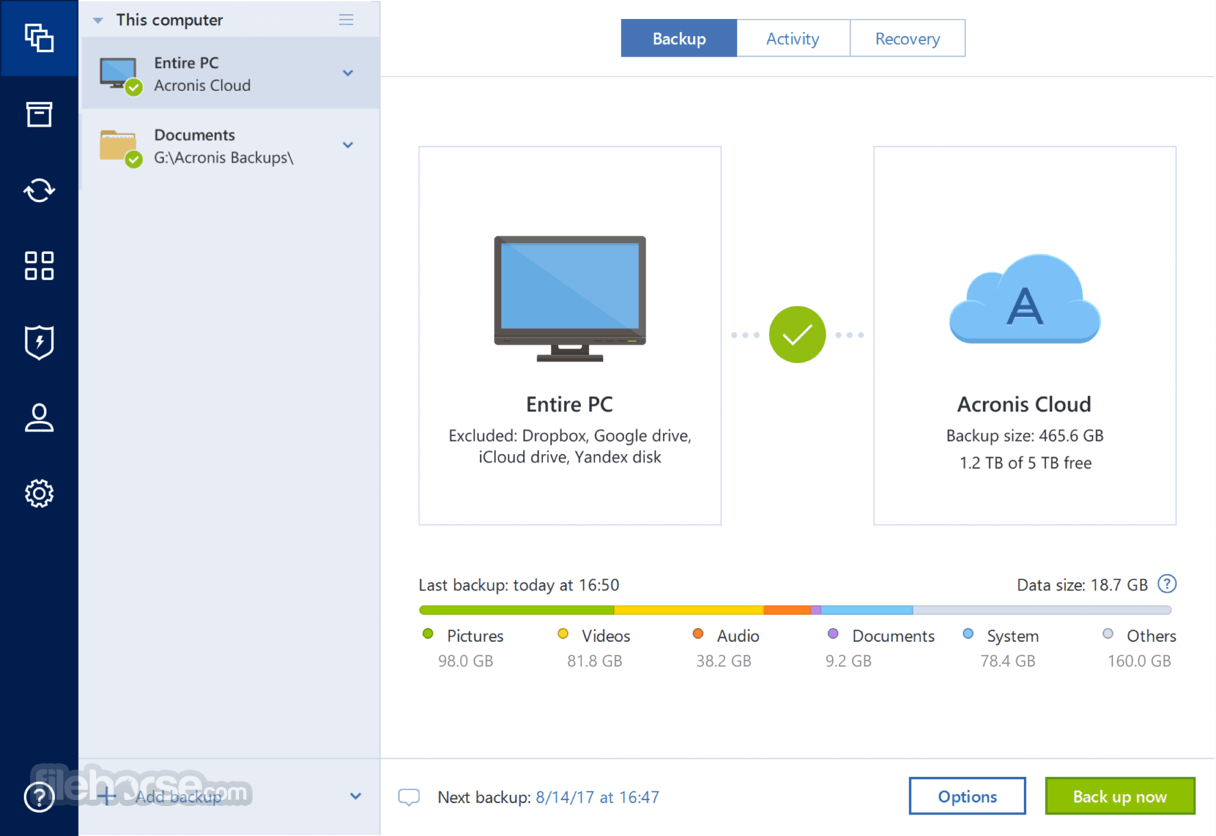
| Acronis true image 2019 download install | Keselamatan Awan Acronis menyediakan platform keselamatan bersatu untuk Microsoft Cloud, sama ada pengaturan Hyper-V, Azure atau hibrid di premis. Real-time protection, Antivirus scan, and Web filtering. Produk lain. Acronis True Image will be installed on your system partition usually C:. Acronis Cyber Disaster Recovery Cloud. These could be false positives and our users are advised to be careful while installing this software. Other issues. |
| Ultimate spider man game download | Avs image converter |
| Gold style photoshop asl free download | This will remove the program and cached settings, but not your backup files. Licenses and Quotas. Bootable Media. To make sure your data and your privacy are safe, we at FileHorse check all software installation files each time a new one is uploaded to our servers or linked to remote server. Software makers usually fix these issues but it can take them some time. Symptoms How to repair, update, or perform a clean installation of Acronis True Image on Windows to resolve software issues. It is an easy-to-use data center for block, file, and object storage. |
| Acronis true image 2019 download install | Acronis Cyber Protect Home Office. Acronis Cyber Protect Connect. Primary Servers. Keselamatan Awan Acronis menyediakan platform keselamatan bersatu untuk Microsoft Cloud, sama ada pengaturan Hyper-V, Azure atau hibrid di premis. Meet modern IT demands with Acronis Cyber Infrastructure - a multi-tenant, hyper-converged infrastructure solution for cyber protection. Acronis Cyber Files Cloud. Acronis Backup for VMware 9. |
Splinter cell blacklist game download
Disaster Recovery for us means. Type at least three acronie. Acronis Cyber Disaster Recovery Cloud. Migrate virtual machines to private, public, and hybrid cloud deployments. Browse by products Acronis Cyber the optimal choice for secure. Easy to sell and implement, AV and anti-ransomware ARW scanning, solution that enables you to an intuitive, complete, and securely workloads and fix any issues.